- Cryptomeria cipher
-
Cryptomeria cipher
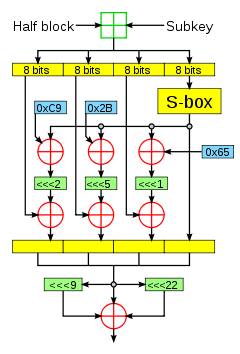
The Feistel function of the Cryptomeria cipher.General Designers 4C Entity First published 2003 Derived from DES Related to CSS Cipher detail Key sizes 56 bits Block sizes 64 bits Structure Feistel network Rounds 10 Best public cryptanalysis A boomerang attack breaks all 10 rounds in 248 time with known S-box, or 253.5 with an unknown S-box, using 244 adaptively chosen plaintexts/ciphertexts.[1] The Cryptomeria cipher, also called C2, is a proprietary block cipher defined and licensed by the 4C Entity. It is the successor to CSS algorithm (used for DVD-Video) and was designed for the CPRM/CPPM digital rights management scheme which are used by DRM-restricted Secure Digital cards and DVD-Audio discs.
Contents
Cipher details
The C2 symmetric key algorithm is a 10-round Feistel cipher. Like DES, it has a key size of 56 bits and a block size of 64 bits. The encryption and decryption algorithms are available for peer review, but implementations require the so-called "secret constant", the values of the substitution box (S-box), which are only available under a license from the 4C Entity.
The 4C Entity licenses a different set of S-boxes for each application (such as DVD-Audio, DVD-Video and CPRM).[2]
Cryptanalysis
In 2008, an attack was published against a reduced 8-round version of Cryptomeria to discover the S-box in a chosen-key scenario. In a practical experiment, the attack succeeded in recovering parts of the S-box in 15 hours of CPU time, using 2 plaintext-ciphertext pairs.[2]
A paper by Julia Borghoff, Lars Knudsen, Gregor Leander and Krystian Matusiewicz in 2009 breaks the full-round cipher in three different scenarios; it presents a 224 time complexity attack to recover the S-box in a chosen-key scenario, a 248 boomerang attack to recover the key with a known S-box using 244 adaptively chosen plaintexts/ciphertexts, and a 253.5 attack when both the key and S-box are unknown.[1]
Distributed brute force cracking effort
Following an announcement by Japanese HDTV broadcasters that they would start broadcasting programs with the copy-once broadcast flag starting with 2004-04-05, a distributed Cryptomeria cipher brute force cracking effort was launched on 2003-12-21. To enforce the broadcast flag, digital video recorders employ CPRM-compatible storage devices, which the project aimed to circumvent. However, the project was ended and declared a failure on 2004-03-08 after searching the entire 56-bit keyspace, failing to turn up a valid key for unknown reasons.[3] Because the attack was based on S-box values from DVD-Audio, it was suggested that CPRM may use different S-boxes.[4]
Another brute force attack to recover DVD-Audio CPPM device keys was mounted on 2009-05-06. The attack was intended to find any of 24570 secret device keys by testing MKB file from Queen "The Game" DVD-Audio disc. On 2009-10-20 such key for column 0 and row 24408 was discovered.
The similar brute force attack to recover DVD-VR CPRM device keys was mounted on 2009-10-20. The attack was intended to find any of 3066 secret device keys by testing MKB from Panasonic LM-AF120LE DVD-RAM disc. On 2009-11-27 such key for column 0 and row 2630 was discovered.
By now the CPPM/CPRM protection scheme is deemed unreliable.
Notes
- ^ a b Julia Borghoff, Lars Knudsen, Gregor Leander, Krystian Matusiewicz. "Cryptanalysis of C2". Extended Abstract (Technical University of Denmark). http://events.iaik.tugraz.at/weworc09/9aa510c7c7aab1/abstracts/04.pdf.
- ^ a b Ralf-Philipp Weimann (2008-03-01). Algebraic Methods in Block Cipher Cryptanalysis. Darmstadt University of Technology. http://tuprints.ulb.tu-darmstadt.de/1362/1/rpwphd.pdf. (Abstract is in German, rest is in English)
- ^ "Distributed C2 Brute Force Attack: Status Page". http://www.marumo.ne.jp/c2/bf/status.html. Retrieved 2006-08-14.
"C2 Brute Force Crack - team timecop". Archived version of cracking team's English web site. Archived from the original on 2005-03-06. http://web.archive.org/web/20050306065032/http://pbx.mine.nu/ch/c2bf/. Retrieved 2006-10-30. - ^ "Discussion about the attack (Archived)". Archived from the original on 2005-03-16. http://web.archive.org/web/20050316033144/http://pbx.mine.nu/ch/test/read.cgi/general/1075424427/. Retrieved 2006-10-30.
References
- (PDF) C2 Block Cipher Specification. 1.0. 4C Entity, LLC. January 17, 2003. http://edipermadi.files.wordpress.com/2008/08/cryptomeria-c2-spec.pdf. Retrieved 2009-02-13.
- "Software Obfuscation from Crackers' Viewpoint" (PDF). Proceedings of the IASTED International Conference. Puerto Vallarta, Mexico. January 23, 2006. http://se.aist-nara.ac.jp/achieve/pdf/118.pdf. Retrieved 2006-08-13.
Categories:- Block ciphers
- Broken block ciphers
- Feistel ciphers
Wikimedia Foundation. 2010.